Last year, 28% of businesses saw an increase in physical security incidents, and 27% said they expected those to continue. However, even knowing the risks, 57% said they had not changed their security strategy. Among those who were increasing security, many were using tools like remote monitoring systems which don’t catch incidents until they happen.
For companies that are serious about making security a priority, policy-based access control (PBAC) is increasingly becoming the gold standard for managing access to a company’s systems. PBAC uses state-of-the-art credentialing and authorization technologies to automate access based on a zero-trust model in which everyone is assumed to be a potential bad actor until they can provide proof that they have the correct permissions.
Below, we’ll look at how PBAC features keep companies safe and lead the way in physical security measures.
Policy-based access control (PBAC) is a way of granting specific types of access to company assets based on a set of rules. These rules can take into account a person’s location, job role, rank, and much more. For example, if a person has management credentials, they may be granted access to certain systems and can perform specific actions that others cannot.
However, a lot more goes into setting up a sophisticated PBAC. It also requires creating multiple steps in a company’s system, such as Policy Enforcement and Decision Points (PEPs and PDPs), which check credentials and generate authorization requests based on very specific attributes and rules.
PBAC systems can use a combination of four types of attributes to determine if a user should be granted access to a system and what they can do once they’re in:
The combination of these attributes with policies is what makes PBAC unique. PBAC uses Boolean logic to parse whether an access request is legitimate and grants only the relevant access if all the conditions are correct. Systems are programmed to process the attributes in an “if, then” fashion – for example, a policy may state that if the person trying to gain access to a file while working from home is a manager and can show credentials (such as a password), then they can access a specific file folder. However, the formulas are typically more complex. For example, if a manager is trying to access a document on the company system, and if they are within a certain geographical area, then they may access and edit a file. But if it is between the hours of 12am and 5am, then they may only see and read the file.
As you can see, this could prevent someone with faulty credentials on the other side of the world from gaining undue access to a system (even if it locks out a manager working late). PBAC can provide more extensive control because it takes attributes and other rules into account but adds an extra layer that allows it to be dynamic.
Role-based access control (RBAC) is quite common in the workplace, but it’s simply not enough to deter savvy bad actors who want access to physical or digital assets. It’s also not flexible enough to offer access to those who need it based on more granular attributes, such as time, device, or location. For example, if all managers are given the same access, an inflexible RBAC policy may bar them from a new location or they may not be able to access company assets when they take on a new task without a title change.
The large categories used by RBACs require someone to constantly track an individual’s status in order to stay up to date. Neglecting to do so can cause both security risks and compliance issues, especially when permissions are not revoked when necessary.
Now that hybrid and remote work are so common, PBAC is more necessary than ever to prevent security incidents that can cause financial and reputational damage. With PBAC, access is provided on a need-to-know only basis, and can be tracked closely.
The pandemic brought sudden workplace closures, changing business hours, and staffing changes that still haven’t entirely returned to normal. This led to major security challenges as companies tried to keep up with how to control building and worksite access. Card-based security can be easily thwarted and typically offers 24/7 access to anyone who holds the card. But the problem can’t be solved by taking away employee access because companies also want workers to be maximally productive, meaning they must balance access with convenience.
PBAC attempts to solve the problem of tracking who gets access to a site or asset, when they have access, and what they can do once they’ve gained access. That access can also be amended in real-time in case of emergencies.
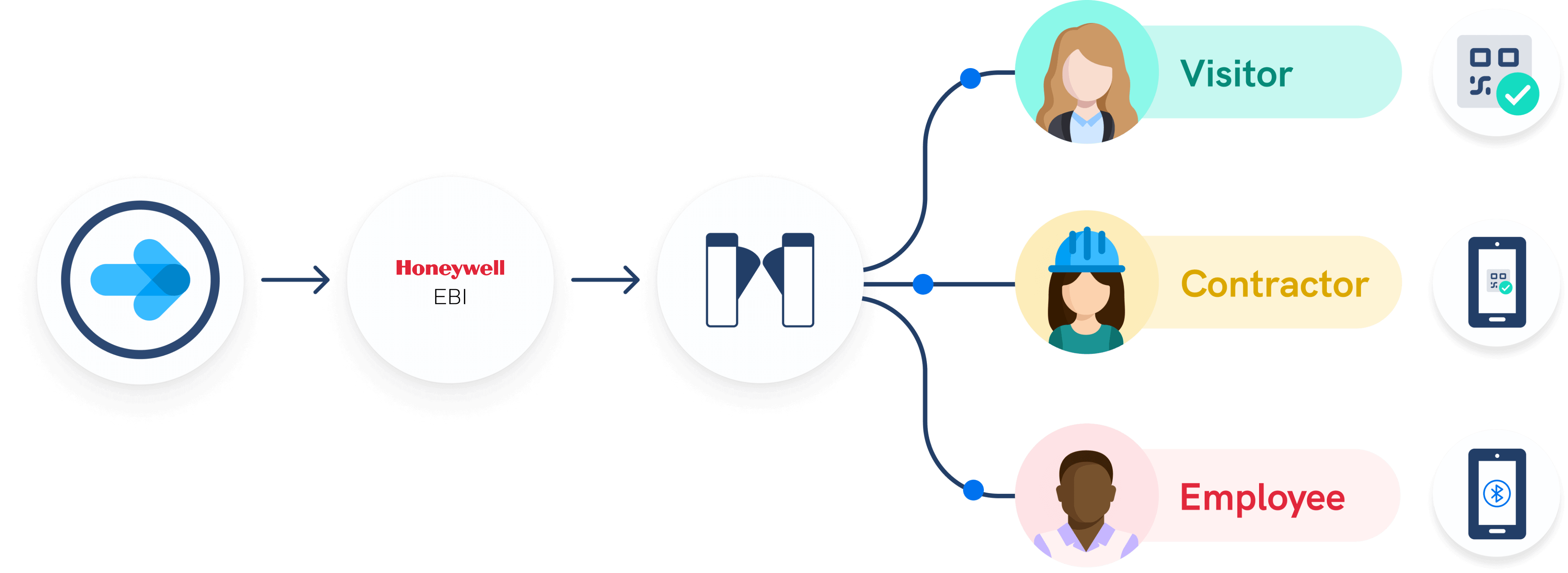
Most access control models use static rules to assign access and ignore the context in which the request is made. Overly broad categories can create security risks, while narrow ones keep employees from accessing the assets they need to do their work.
Access control solutions work in tandem with visitor management systems (VMS). A VMS such as Sine’s can scan in employees and visitors to check credentials, help employ geofencing to restrict access to certain parts of a work site, and be integrated into an access control system, such as the one offered by our partner, Gallagher. The use of QR codes, host notifications, and pre-registration are all points at which policies can be put in place to stop people from accessing sites where they shouldn’t be.
Interested in learning how to protect your business with Sine? Book a live demo with one of our product experts to find out how to get state-of-the-art physical security for your work sites.
As a business, getting customers, clients and contractors through your doors as seamlessly as possible should be a top priority. If you’re making use of a visitor management system, it’s suggested that you make use of the integrations that come with it.
For example, if you’re looking to have all of your check-in data automatically added to contractor management proceedings, or would like to see access control made more secure, then integrations can be most effective way to do this.
Below we’ll take a look at a few essential integrations that can help streamline check-in and can give your business the vital details and information it needs to improve efficiency.
From a business standpoint, integrations are supported applications or services that work with your existing visitor management system – similar to a plug-in.
When a visitor, client or contractor checks into your business, these integrations work seamlessly to provide them access to an office, or even share important events with them. Think of these integrations as a way that can help automate almost all entry and data collection and utilisation procedures.
To add, these integrations work from the outset, so long as they’re correctly added. Once you launch a visitor management system such as Sine, you can add all of your staff details, allowing them easy entry with little slowdown — keeping things moving.
Although there are an array of Integrations making changes for all types of businesses, there are a few fundamental ones that all companies should be making use of. A few of these key Sine Integrations are outlined below, along with their best perks.
Up first comes an integral integration suite — one that can keep check-ins safe, and moving without the need for paper. We’re glad to say that gone are the days of scouring for names and registered employees on paper sheets. With access control integrations, finding visitors or registering staff can be just a QR scan away.
All attendees and expected guests, staff and contractors are automatically added to a database, waiting to be checked in for work or an event.
Sine integrates with:

These integrations make it possible for businesses to quickly see all essential data on contractors entering and leaving the workplace. To add, these may provide the necessary data to ensure compliance, hours worked and more, keeping everyone accountable. Contractor management integrations merge all check-in and check-out data to help keep a detailed log of all time spent on site.
In addition to these perks, contractor management integrations can enable induction sharing and site rejection, keeping site access open only to those who require it for a specific task.
Sine integrates with:
Without a doubt, keeping filled in at all times with real-time information is a workplace essential that can’t be negotiated. Thankfully, Integrations can enable workplace notifications that can help keep all business managers, staff and contractors in the loop. You’re able to see when visitors check-in and reject or accept their registration right there and then via Slack or Microsoft Teams.
These integrations can allow for a much smoother check-in process for everyone, as real-time notifications give you the chance to approve or deny check-in in an instant, no more wait times.
Sine integrates with:
For businesses who share essential data via Local Area Networks or LAN networks, automation in Wi-Fi sharing can be a saving grace when it comes to efficiency. Integration through Aruba ClearPass help enable secure Wi-Fi provisioning, keeping everyone connected from the moment they step into the workplace.
Within these integrations, there's also easy way to see what staff and visitors are doing online, keeping an eye on site-wide bandwidth use.
Sine integrates with:
Key Cabinets
Sine integrates with quality platforms to help simplify your key management and keep your workplace running effectively. Sine integrates with platforms such as KeyWatcher and Torus that can help provide a seamless, automated key management solution, creating a frictionless check-in experience for your visitors.
These integrations can enhance compliance from visitors and enables visibility across all visitors and keys, even with multiple sites.
Sine integrates with:
Watchlists can be further enhanced through our integrations, available to synchronise your watchlist with screening platforms, such as Descartes MK Denial.
To add to security, MK Denial automates the audit trail by delving into an array of databases, searching for those requesting access to a worksite. All staff will be vetted effortlessly and the MK Denial integration also provides data and enough insight to block site access to specific staff members or visitors.

For an excellent and comprehensively automated management solution, there are a few other integrations that can be considered.
With an integration by Procore, workplace managers can take a company-wide view of contractor attendance and delve into real-time hourly data. To add, Procore also writes and stores hours-worked information and check-in and check-out logs, helping keep managers in the loop about when contractors arrived and left a site.
In some cases, organisations may require their visitor management systems to be as customisable a possible, and through Webhooks this is effortless. Managers are able to create custom workflows that are activated in specific circumstances and rolled out to iPad and smartphones.
Sifting through hundreds of event registrations may be time-consuming and destroys the flow of your event. Not to mention the risk of receiving negative feedback with long and unorganized queues. With the Eventbrite integration, you can eliminate that risk and streamline your check-in process.
For each event in Eventbrite, attendees get a ticket for registration. Eventbrite automatically collects the attendee’s name, email, and phone number. It allows you to manage all of the attendance side of the events you’re hosting. Including ticketing, marketing, and attendee lists.
With security and entry control being a prime focus for business managers, directory integrations can be very important. Through Active Directory, you’re able to populate your entire Sine system with staff members and contractor data. This allows Sine implementation across a number of workplaces, in just a few clicks.
Through Integrations with Sine, it can be easier than ever to streamline, secure and record the check-in process for businesses of all types.
Sine integrates with a variety of contractor management platforms to allow businesses to quickly see all essential data on contractors entering and leaving the workplace, strengthening compliance and accountability among your workplace. Moreover, these integrations enable induction sharing and site rejection, helping to keep site access only open to only those requiring it for a specific task.
Find out what integrations Sine partners with and how they can help safeguard your workplace and enhance compliance from contractors and staff.

The Sine + Altora integration works seamlessly together to ensure contractor compliance. Ensure that every contractor has filled out your required induction process. Then, with Sine Core, you will be able to approve or reject their application based on the information provided. You can induct contractors upon check-in and reject non-inducted contractors. You can then require them to complete any required inductions before check-in approval. This can give you full visibility over your contractors who have checked in through analytics and reporting on the Altora dashboard.
The Sine + Browz integration simplifies contractor management, ensuring that every contractor entering your site is cleared to start work. You can set up inductions, permits to work and SWMS to ensure you are working with safe, qualified, and responsible contractors. Regardless of the number of sites, the Sine + Browz integration helps makes contractor management simple and easy. You can even approve or deny entry right from the Sine dashboard, even if you aren't on-site!
The Sine + Kineo integration makes it easy to check your contractor’s verification status, account validity, and status of their course completion for any number of Kineo units. Whenever a contractor attempts to check in, they are sent the workflows required before the approval of an access request can be granted. This is then checked against the Kineo database and once check-in is successful, a notification is sent to the site host. No matter if a site is manned or unmanned, the Sine + Kineo integration can help make managing your site simple and easy!
Find out how Sine can streamline contractor management for your site and take the hassle out of induction processes by booking a demo with our team today!